LDAP Configuration¶
You can connect Allegra to a directory server (LDAP, Active Directory) to centrally manage passwords. You can also register users in the LDAP directory from Allegra and change passwords. Thus, Allegra offers you a complete system for self-registration and password management.
To connect Allegra to one or more directory servers, as a system administrator, go to the Administration View > Server Administration > LDAP & SSO.
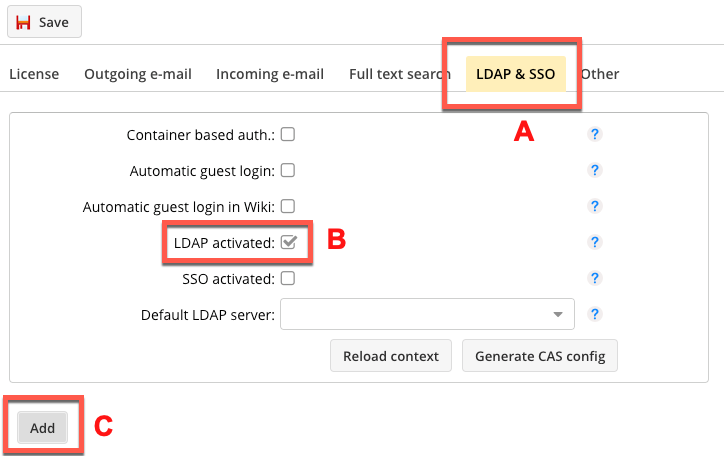
Select the checkbox for LDAP (B) and click the button (C) to add a connection. You can also configure multiple connections, for example, if you want to integrate employees from a large company coming from different regions without having to open the entire parent directory tree. Or you can set the base DN once on the list of users and once on groups and organizational units.
LDAP connection settings¶
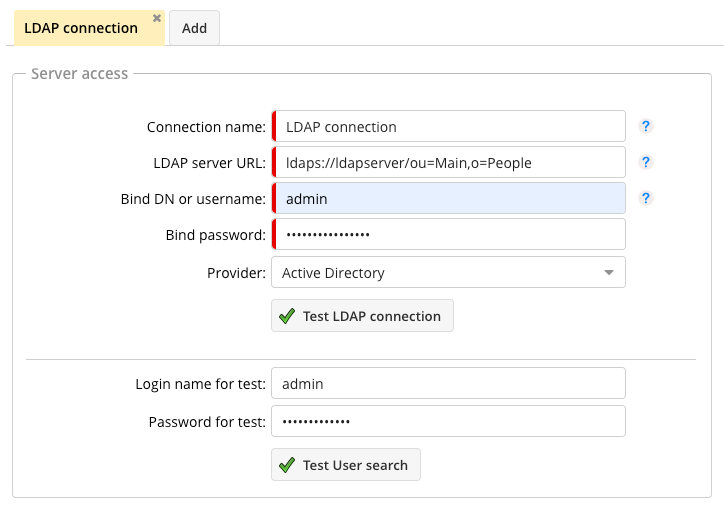
The “Bind” username and password are required to be allowed to look into the directory server at all. For “anonymous bind”, these fields are left empty.
LDAP schema position¶
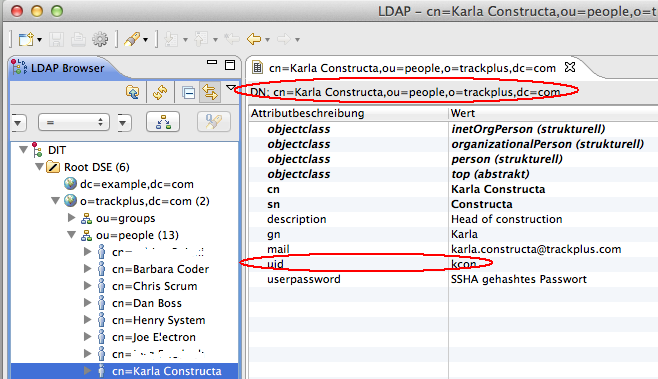
The required entries can be easily determined by using a browser for the LDAP server, such as Apache Directory Studio.
LDAP synchronization¶
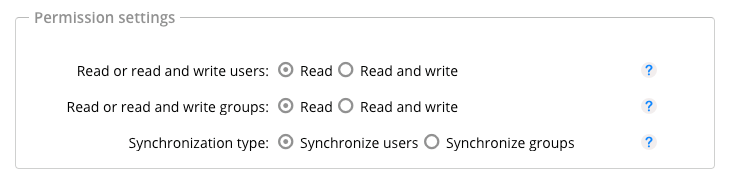
Here you can set how Allegra users should be synchronized with the directory server. Both users or groups can be synchronized. If there is read-only access, users from the directory server will be created in Allegra, but not vice versa. If there is read and write access, users or groups in Allegra are also created in the directory server.
LDAP user and group schema setting¶
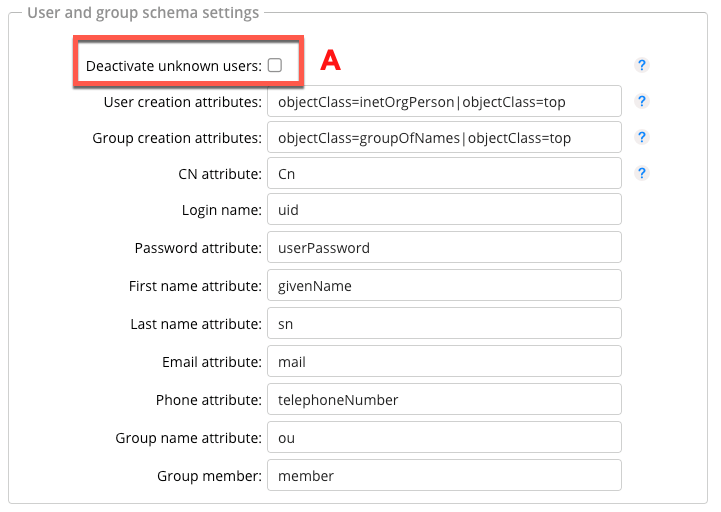
The checkbox (A) determines whether users that are not found in the directory server should be disabled. The users “admin” and “guest” are excluded from this. By selecting the correct server type (e.g., Open LDAP, Active Directory, etc.) above, you can set useful defaults in this workspace.
LDAPS with self-signed certificates¶
Allegra also supports the secure LDAPS protocol. To run LDAPS with official certificates,
you just need to specify “ldaps” instead of “ldap” at the beginning of the URL for the directory server. To use
self-signed certificates, you must create an ldaps keystore file named
“Trackplus.ks” in the TRACKPLUS_HOME directory, subdirectory “Keystore”.
This item is described in detail in section “Using SSL and TLS Encryption on Email and LDAP Connections”. The LDAP server
must also be configured for LDAPS.
For a Windows server, we had to change the ApacheDS configuration file as follows:
<!-- SSL properties -->
<property name="enableLdaps" value="true" />
<property name="ldapsPort" value="10636" />
<property name="ldapsCertificateFile"
value="C:\jdk1.5.0\bin\zanzibar.ks" />
<property name="ldapsCertificatePassword" value="secret" />
<bean id="configuration"
class="org.apache.directory.server.\
configuration.MutableServerStartupConfiguration">
and
<property name="workingDirectory" value="example.com" />
<!-- SSL properties -->
<property name="enableLdaps" value="true" />
<property name="ldapsPort" value="10636" />
<property name="ldapsCertificateFile"
value="C:\jdk1.6.0\bin\zanzibar.ks" />
<property name="ldapsCertificatePassword" value="secret" />